Vulnerability Assessments
Threats
This process identifies and ranks network vulnerabilities in order of greatest risk reduction benefit for remedy. It also involves
establishing corrective measures for vulnerabilities discovered throughout the evaluation; frequently, this entails
applying a patch or containing an asset.
Why Are Vulnerability Assessments
Important?
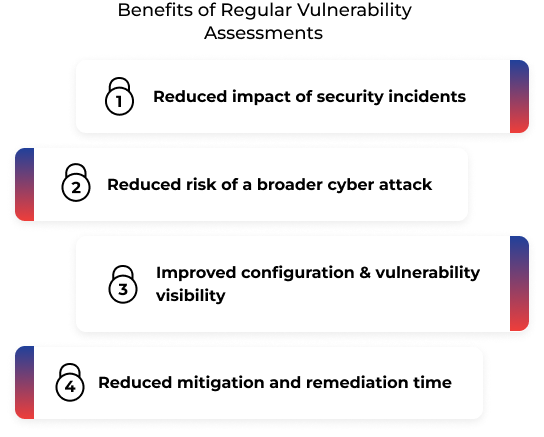
A thorough vulnerability assessment gives security teams crucial information on the network’s and IT infrastructure’s weaknesses. Security teams can effectively manage and patch network vulnerabilities thanks to vulnerability assessment, which shields companies from threat actors and potential breaches.
A network breach may have far-reaching effects, starting with the months or even years it may take to find all affected assets and ending with harm to your company’s reputation. Vulnerability assessments should be carried out on a regular basis to ensure that your network is properly secured.
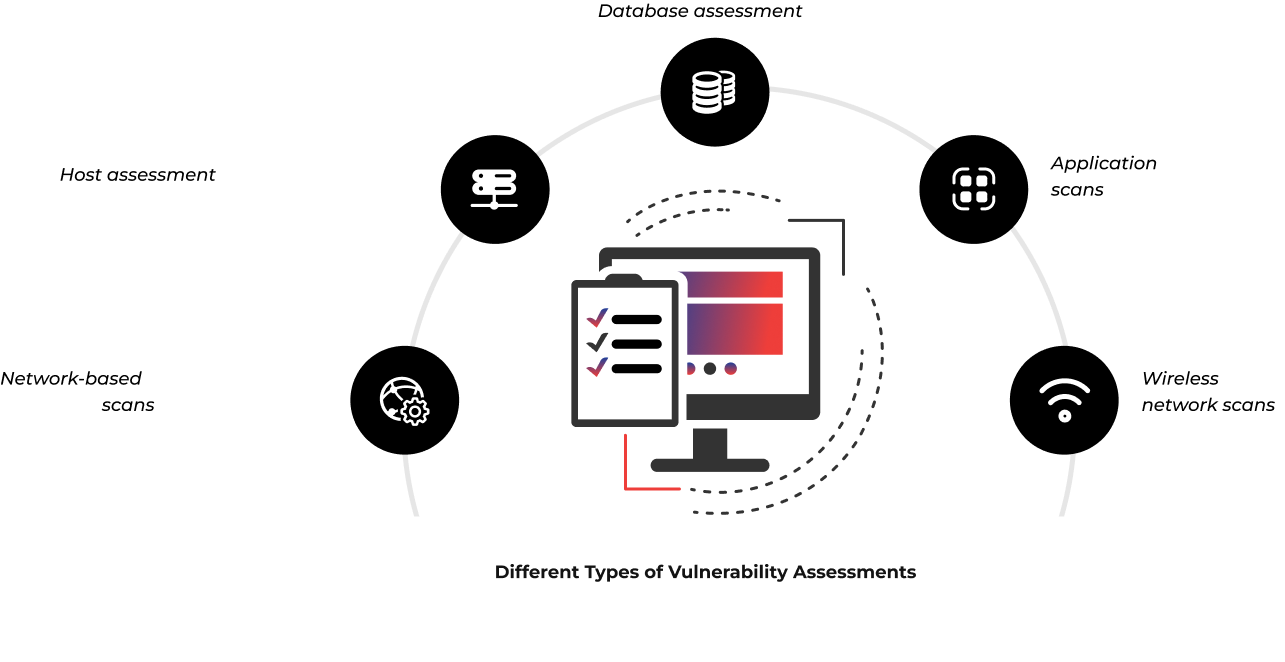
Our Vulnerability Assessment Services
Why GoAllSecure for Network Vulnerability Assessment?
Is the IT infrastructure of your business susceptible to attacks from nefarious outsiders? Is the security of your data guaranteed? With the aid of GoAllSecure’s vulnerability assessment services, you can map out a prioritised road to better cyber security for your company and get the answers to these vital questions.
Our specialists will assess your defensive security posture using industry-standard assessment methods and manual attack methodologies designed to find flaws that are frequently missed with just automated vulnerability scanning.
To ensure that you have the knowledge necessary to prioritise repair activities, we offer remediation assistance and risk grading in addition to reporting on the vulnerabilities we find.
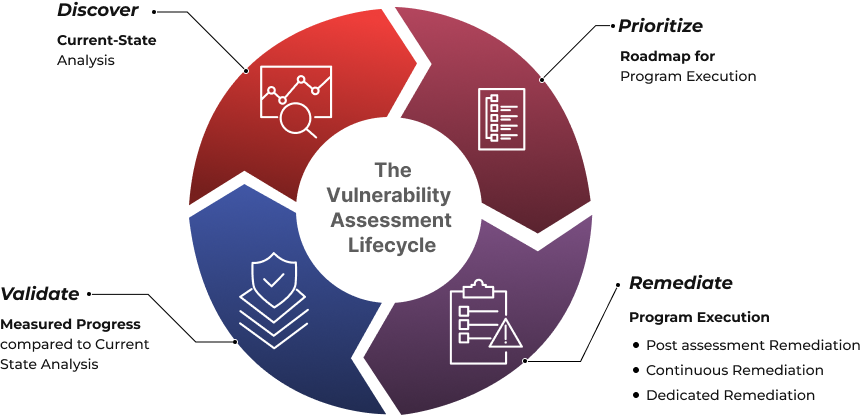
Our Vulnerability Assessment Process
Identifying the Vulnerabilities
The first step of the process is vulnerability testing and
identification. This step’s goal is to create a thorough list of
vulnerabilities by using automated methods to scan them or
manually testing and evaluating them. Our security analysts
determine whether applications, servers, or other systems are
secure. To find security flaws, analysts also use vulnerability
databases, vendor vulnerability bulletins, asset management
systems, and threat intelligence feeds.

Analysing the Discoveries
Next in the vulnerability assessment process is the analysis of
vulnerabilities. Finding the source and underlying cause of the
vulnerabilities found in step one is the goal of this stage.It entails
determining the system elements that are vulnerable and finding
the underlying cause for each vulnerability. For instance, an
outdated open-source library could be the source of a
vulnerability. This offers a direct route for corrective action, i.e.,
upgrading the library

Prioritising Based on Risk
The step of prioritising vulnerabilities is aimed at ranking every
finding from most to least risky. Our security analysts score each
vulnerability according to many criteria, including
- Systems that are impacted
- Which data is in danger
- Which corporate functions are in danger
- The simplicity of compromise or attack
- The magnitude of an assault
- Potential harm brought on by the vulnerability

Remediation
Remediation is the process of closing security gaps. Our team of
experts often works together to devise the best course of action
for fixing or mitigating each vulnerability. Remedial actions in detail include
- New security procedures, measures, or tools are introduced
- Upgrading operational or configuration alterations
- Creation and application of a security patch

task. We advise them to carry it out at regular intervals for it to be effective.
Better Secure Your Organisation

















 TRAVEL & HOSPITALITY
TRAVEL & HOSPITALITY HEALTHCARE
HEALTHCARE RETAILS & ECOMMERCE
RETAILS & ECOMMERCE BANKING & FINANCIAL
BANKING & FINANCIAL AutoMobile
AutoMobile MANUFACTURING
MANUFACTURING FOOD
FOOD EDUCATION
EDUCATION


