Red Team Exercises
A Realistic Approach to the Security Testing
Option
threat to your organisation, targeting all possible elements, including the cyber assets,
the personnel that work for your organisation, and the physical assets. This assessment
is a simulation of a sophisticated attack against your organisation, where a variety of
tactics, techniques, and procedures will be used.
What is a Red Team Exercise?
scenario-based controlled incidents. Red teaming goes above and beyond vulnerability assessments and penetration
testing, as it takes all components within the organisation into scope and has a realistic scenario-based approach.
Ultimately, red teaming allows organisations to mature their cyber capabilities and kick-start transformation programmes.
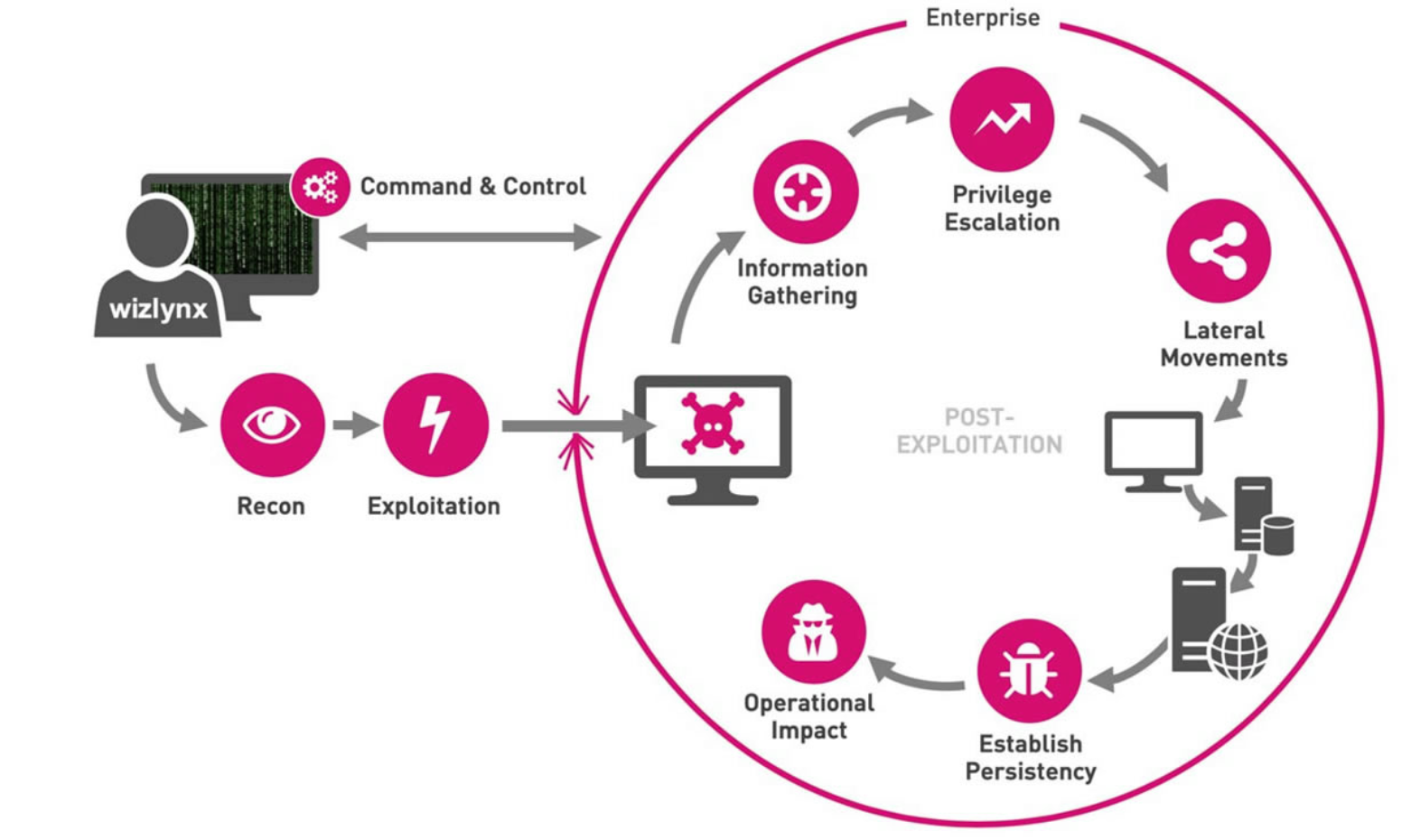
and how to remain cyber resilient by empowering your blue teams is a key outcome of a successful
red team assessment
Tools and Techniques Used in Our Red-Team Exercises
Red teams will attempt to apply the same tools and strategies that actual attackers use. However, red teamers don’t harm anything, unlike cybercriminals. Instead, they highlight gaps in a company’s security safeguards.
Strategic Thinking
The ability to think laterally and challenge
long-standing assumptions
Industry Knowledge
Expert-level knowledge of all the latest
threats and vulnerabilities
Physical Attacks
Finding weaknesses in physical security
systems and defence
Open-Source Intelligence
Using publicly available information to
gain an advantage
Tactical Planning
Devising, coordinating, and executing a
plan to perfection
Social Engineering
Exploiting innate human vulnerabilities
to leverage attacks
Cyber Attacks
Using a cybersecurity arsenal to access
confidential systems and data
Credential Brute Forcing
Consistently guessing passwords, for
instance by attempting credentials from
breach dumps or lists of frequently used
passwords.
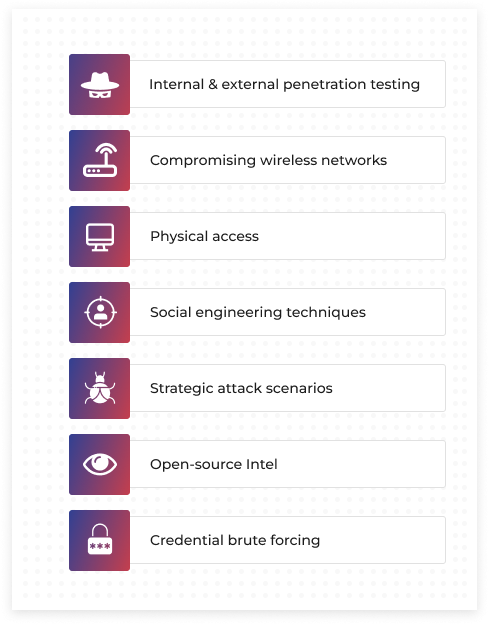
Test Your Organisation’s Resilience Against Sophisticated Threat Actors
Why Do You Need Better Red Team Exercises?
assets are most enticing to threat actors, as well as developing the ability to detect, all while guaranteeing a quick and
effective response
and the structure collapses. “
(and maybe haphazardly) applied, and compliance should be the result of the strategy rather than its sole
objective.
Speak to a Red Team Exercise Expert for Holistic Threat Protection

















 TRAVEL & HOSPITALITY
TRAVEL & HOSPITALITY HEALTHCARE
HEALTHCARE RETAILS & ECOMMERCE
RETAILS & ECOMMERCE BANKING & FINANCIAL
BANKING & FINANCIAL AutoMobile
AutoMobile MANUFACTURING
MANUFACTURING FOOD
FOOD EDUCATION
EDUCATION


