iOS Application
Penetration Testing
iOS Pen-Tests That Detect Vulnerabilities and Give
You Full Visibility
iOS application penetration testing is the practice of evaluating the security of an iOS application to find gaps and flaws
that attackers may be able to take advantage of. This technique involves utilising an automated tool or decompiling the
application to find any flaws that might result in bugs. The tests range from installation and configuration to
discovering and exploiting software and hardware vulnerabilities to strengthen network security and eliminate flaws in
the iOS operating system.
that attackers may be able to take advantage of. This technique involves utilising an automated tool or decompiling the
application to find any flaws that might result in bugs. The tests range from installation and configuration to
discovering and exploiting software and hardware vulnerabilities to strengthen network security and eliminate flaws in
the iOS operating system.
Why Is iOS Application
Penetration Testing Important?
iOS penetration testing is performed to identify vulnerabilities or security weaknesses that can be exploited in applications. Any security audit must include an iOS penetration test.
iOS penetration testing enables you to examine all the applications’ security features and make sure there are no security flaws. This will allow you to verify that there are no vulnerabilities to exploit in your application. Some of these weaknesses could lead to data theft, information leakage, and even the loss of sensitive data, all of which would be devastating for the company.
iOS penetration testing enables you to examine all the applications’ security features and make sure there are no security flaws. This will allow you to verify that there are no vulnerabilities to exploit in your application. Some of these weaknesses could lead to data theft, information leakage, and even the loss of sensitive data, all of which would be devastating for the company.

Our Tried and Tested iOS Penetration
Methodology
At GoAllSecure we examine how an iOS application responds to typical input attacks, server-side controls, data
connection pathways, and client-related concerns as part of our assessment process.
connection pathways, and client-related concerns as part of our assessment process.
The iOS application’s architecture is examined by our penetration testers. The pentest team then plans how to access
the application and how to realistically replicate attacks against it. Next, the team starts automated scanners in the
background to look for application vulnerabilities. Attacks are launched in real-time to learn how the application
behaves. The publicly accessible CVEs for known components are also tested.
the application and how to realistically replicate attacks against it. Next, the team starts automated scanners in the
background to look for application vulnerabilities. Attacks are launched in real-time to learn how the application
behaves. The publicly accessible CVEs for known components are also tested.
Last, the team compiles a list of CVEs that were exploited along with a summary of the attacks that were undertaken.
The report also includes suggestions on how to remedy the vulnerabilities.
The report also includes suggestions on how to remedy the vulnerabilities.
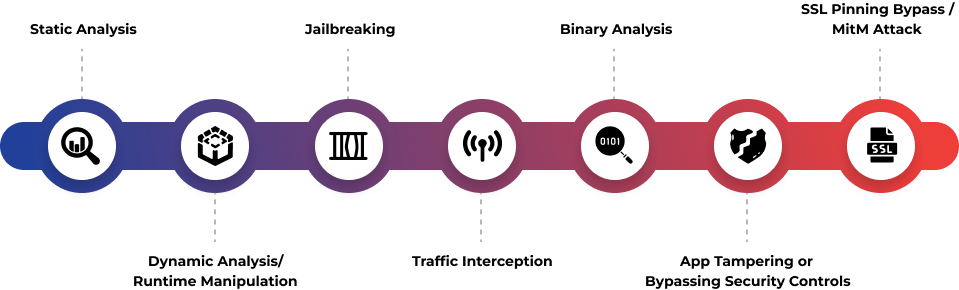
What are the key
areas of focus in iOS
Application
Penetration Testing
Network Communication
Broken Cryptography
Data Storage
User Authentication &
Authorization
Secure Coding Practices
Session
Management
Error Handling & Logging
Third-Party Library Usage
API Testing
Compliance with Security
Standards & Guidelines
Input Validation & Output
Encoding
Perform 360° Security Checks for Your iOS
Apps and Protect Them from Breaches
Basics of an iOS Application
iOS applications communicate with hardware through a number of well-defined system interfaces. These interfaces offer translation for programs that might use different kinds of hardware. This makes the development process go more smoothly as a result.
The iOS system’s basic architecture is shown in the diagram below, where multiple layers are used to create communication and carry out various functions between the Application and Hardware levels.
The iOS system’s basic architecture is shown in the diagram below, where multiple layers are used to create communication and carry out various functions between the Application and Hardware levels.
What to Expect with
GoAllSecure’s iOS Pentesting
Service
The iOS application attack surface consists of all components
of the application, including the supportive material
necessary to release the app and support its functioning.
of the application, including the supportive material
necessary to release the app and support its functioning.
Mobile App Authentication
Architectures
iOS Anti-Reversing Defenses
Network Communication
Network APIs
Data Storage on iOS
iOS Platform APIs
Data Storage on iOS
Code Quality & Build Settings
for iOS Apps
Local Authentication on iOS
Tampering and Reverse
Engineering on iOS
Looking for iOS Application Pen Testing Services?
Let’s Start the Conversation Today!
Let’s Start the Conversation Today!

















 TRAVEL & HOSPITALITY
TRAVEL & HOSPITALITY HEALTHCARE
HEALTHCARE RETAILS & ECOMMERCE
RETAILS & ECOMMERCE BANKING & FINANCIAL
BANKING & FINANCIAL AutoMobile
AutoMobile MANUFACTURING
MANUFACTURING FOOD
FOOD EDUCATION
EDUCATION


